Access Control
A novel solution for interlocking doors
We recently built a new access control solution for a life sciences company’s sterile lab environment, using a particularly elegant technical approach.
This client’s 10-room clean area included multiple interlocking doors with and without card access, and one three-door interlock. In this application we were asked to account for omni-directional and bi-directional traffic for areas of gowning, de-gowning, material handling, waste handling, and pressurized cross-contamination.

Customarily, a piece of hardware such as Von Duprin’s 9400 series interlock controller could be used to interlock multiple doors. These tried-and-true controllers offer several attractive features like expandability and a FAI (Fire Alarm Interface) input. (Both require additional hardware). In the case of multiple interlock spaces, each would need a dedicated controller and FAI input. Interlock controllers also need a sizable amount of space local to the doors and a dedicated high voltage power source.
One feasible alternative to that method would be to use an access control platform such as Genetec to collect a variety of inputs, and create a custom macro to determine the sequence of operations. The access control platform method is effective if your software interface allows enough flexibility to handle the programming. Yet the additional hardware costs and lack of open-ended programming on systems like Lenel and Software House make it hard to develop a standard process.
Secuni’s engineers instead developed a new solution utilizing PLCs (Programming Logic Controllers) designed by Automation Direct.
PLCs are typically utilized in HVAC and BAS systems. These small format modular units can be nested neatly inside of a power enclosure. The PLC utilizes the low voltage (24v) provided by any ACP to supervise inputs from several sources including door status, bond status, entry/exit requests, emergency over-rides, and any other environmental condition (pressure/temperature/vapor detection) which can be indicated by outputs from external devices.
Here’s a partial schematic from our as-built drawing, showing the PLCs.
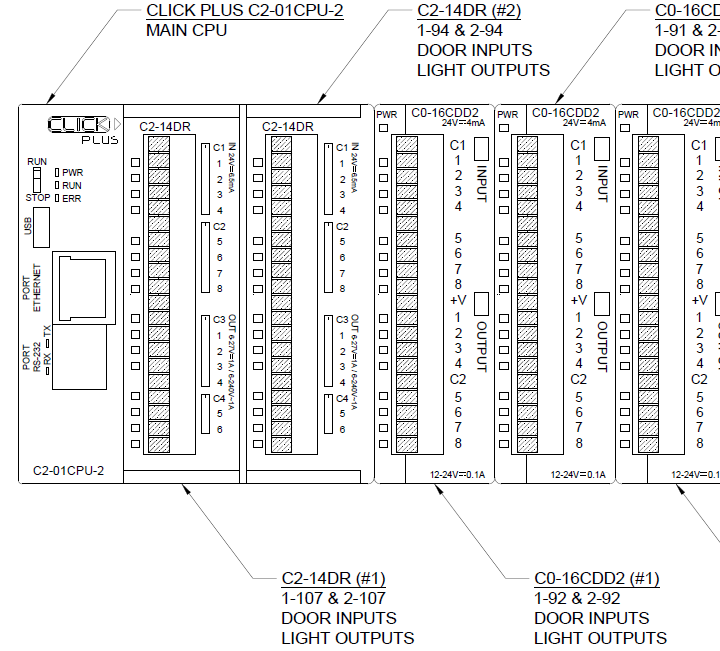
PLCs collect analog or digital input signals from multiple devices. These “events” can then be used to write custom programming sequences, which produce “actions” in the form of digital or analog outputs.
This approach allows for a consistent standardized approach to complex interlock solutions regardless of access control platform. PLCs also offer a significant cost reduction on the hardware side. Card access doors will still require a door controller, but non-card access doors will not require additional licensed hardware.
Cost savings are case by case depending on scope and system but will be quite meaningful considering the lack of licensing, need for electrician, and hardware costs.
We believe this method saved the client $50,000 over the customary interlocking door technical approaches.
PLCs can be monitored via network connection or function completely off-line in areas of concern. PLCs can also live on a BacNet protocol for automations integrations or be linked on a RS-485 Comm protocol.
One CPU can handle up to 8 downstream controllers, which means 8 interlocked areas with basic config.
PLCs programming can be stored onboard the CPU with back-ups loaded on the mounted SD slot or USB stick. Programming can be done directly via network/serial ports or remotely via IP interface.
How You Can Respond to the Flipper Zero Threat
A $100 handheld consumer-friendly device named the Flipper Zero got our attention in 2022, when its Kickstarter was a viral success.

Its continued popularity more recently got the attention of the New Jersey government, who correctly called it a potential threat to any company or school with access cards.
For those new to the topic: In the hands of a moderately tech-savvy person, it can be configured to copy the digital credentials from someone else’s access card. This almost always happens without permission. Once the other person’s credentials are on the Flipper Zero, then the bad actor can gain unauthorized access to your premises.
Card-copying, an established technology, is now packaged in consumer-friendly devices and thus much more of a threat to certain access control systems.
125kHz “Prox” card systems are the most vulnerable and you should plan your eventual migration away from them.
The most popular upgrade path is to switch over to 13.56MHz “Smart” cards, which come in various crytographic strengths:
- NXP’s Mifare Classic/Plus/DESFire/DESFireEV3
- HID’s iClass Legacy/SE/SEOS
At this writing, the first two of each type have been cracked. DESFireEV3 and SEOS are the most secure.
We can help review your card access system vulnerabilities, and create a roadmap to a more secure state.
Roadmap Considerations
Card Readers. You may need to upgrade the readers at each door, replacing or reprogramming them with multiclass readers which handle both kinds of cards (Prox and Smart) and mobile credentials. New cards can be issued once all the readers are installed and active, and the prox cards disabled. The capital expenditure can be spread out by doing it in stages, which can be somewhat more complicated in large-population corporate campuses and universities.
Credentials. Physical cards are a good solution, but the case for switching to mobile credentials has been improving. They are fundamentally more secure than cards (with two-factor authentication), can be provisioned remotely and in stages, and are more extensible. Mobile makes sense right now for smaller organizations (in terms of doors and people), but the economics at scale has been improving quickly.
Multipurpose cards. Universities and colleges often issue cards that work for doors, lockers, POS/vending, the library, and so on. It’s very convenient for the user, but moving to a less-crackable card system takes more effort to get the systems in sync.
High-traffic areas. The low-latency symmetric encryption in the vast majority of card access systems allows people to move through turnstiles quickly. Mobile credentials act somewhat slower, which may be a concern for high-flow areas. We are seeing good biometric (face identification) solutions in the market, and over time expect less user resistance to the technology.
Centralizing Your Security Systems
It’s common for large companies with multiple facilities in the US (and overseas) to have a fragmented set of security systems at all those sites. You might have several kinds of video surveillance solutions running at the same time, and access control systems that don’t talk to each other or your HR database.
How Managed Services Improve Your Security System’s Uptime
This is part of our series on how a managed services team helps your system deliver the required level of corporate safety and security.
(If you’re new to this series, a third-party “managed services team” is a remote set of security experts who assume responsibility for your security system’s day-to-day operation. Here’s our team.)
Today, we’ll focus on how they help deliver a high level of system uptime.
Our Perspective on Open Architecture
We firmly believe in the long-term value of using open-architecture security hardware and software. In other words, fundamentally extensible components that can easily integrate together.
In contrast, some security product lines lock users into a proprietary platform. This may meet your requirements and save capital expenditure in the first few years, but at the cost of higher operating expense and narrowed future choices.
Systems based on open architecture can accommodate new innovations faster, easier, and at lower cost.
